Tenable CTF 2022: OSINT
Find Me if You Can⌗

Answer⌗
Used a lot of time to figure out the meaning of 2 images, but also no clues.
So went to revisit the OSINT question of Tenable CTF last year and found it’s quite easy. It also provides a thinking to solve: use google to search “Tenable” with the description of the image(should be a name of vulnerabilities), and the flag should be hiden in one of those Tenable blogs.
After few attempts, found “homer spring” and “4 shells” should combine to spring4shell, then find this article from Google.
https://www.tenable.com/blog/spring4shell-faq-spring-framework-remote-code-execution-vulnerability
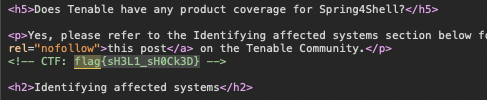
The flag is hiden in source code.
Can You Dig it?⌗


Answer⌗
Drop both images into Google Images and find “SOMETIMES IT JUST CLICKS” should be added to the original one. And the hint is quite obvious as it highlighted CLICKS and ZERO for 3 times.
So use Google to search “Tenable zero click” and find this article:
https://www.tenable.com/blog/cve-2022-30190-zero-click-zero-day-in-msdt-exploited-in-the-wild
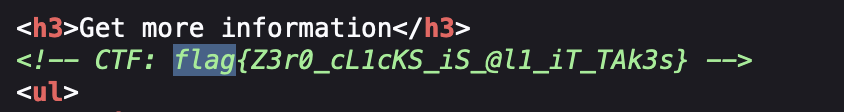
The flag is hiden in the source code.
Lets Network⌗
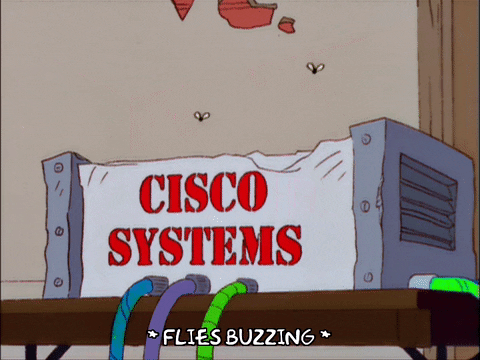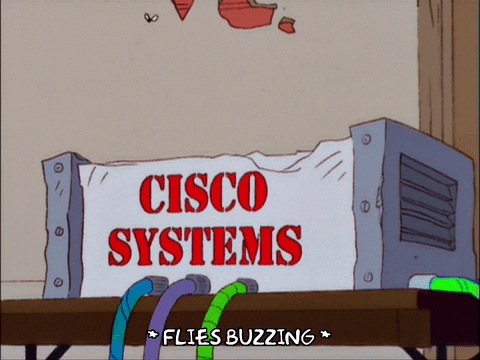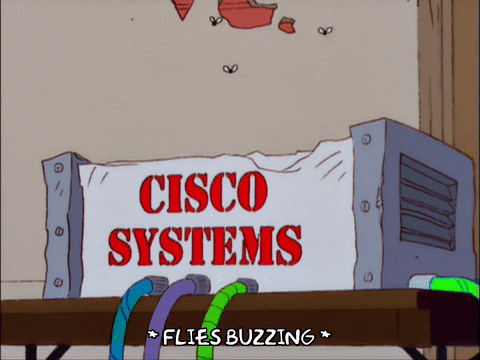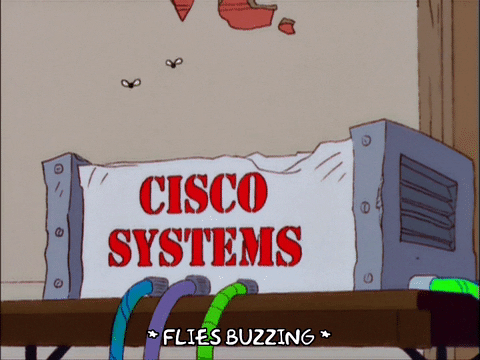

Answer⌗
Images with text again! Just like the previous one, use the keywords “Tenable cisco rv blog” to search on Google, and find the article:
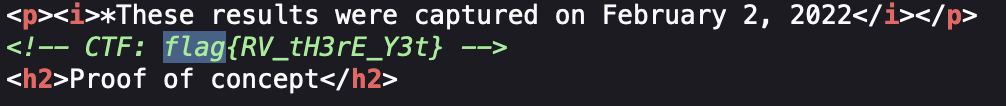
The flag is also hiden in the source code.
Back Then⌗
One of our employees reported this phishing email. Find out who was resonsible for it and see if any of their colleagues have any information we can use on them.
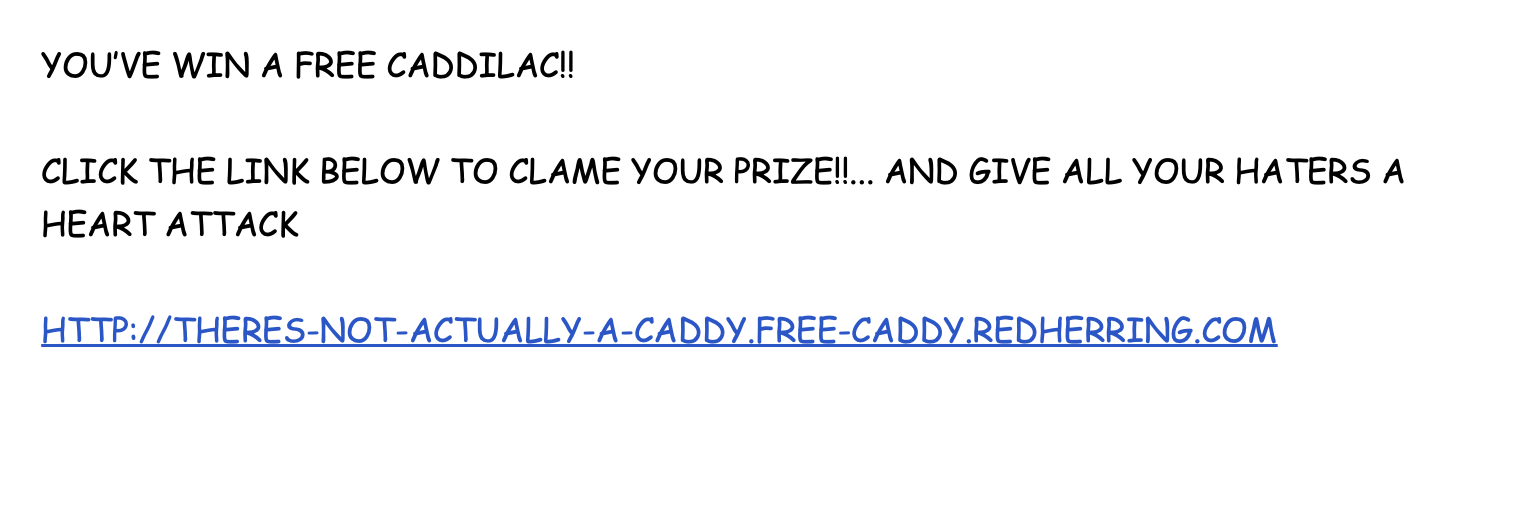
Answer⌗
Open the phishing_attempt.pdf and click on the link, could find it goes to tenable-ctf.io. Then tried few whois providers to check if there is any personnel information left but seems all information are being “REDACTED FOR PRIVACY”.
Check for the first hint, it asked to search from some 3rd party which may have cache. Find this domain is registered on Namecheap. Go to the whois page on Namecheap and find the registrant information:
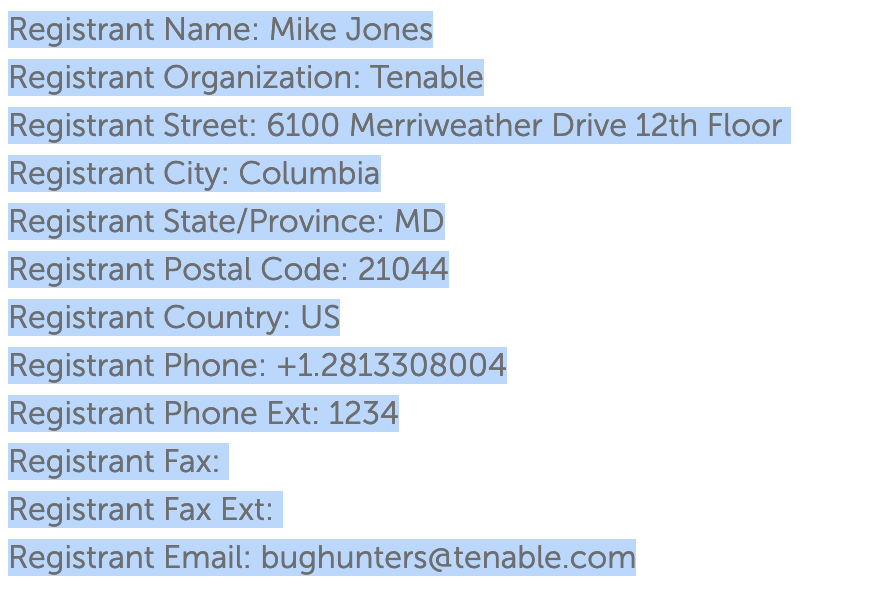
Now get the name, email and phone number, then use it to search on LinkedIn as it is mentioned to find his “colleagues” and find this.
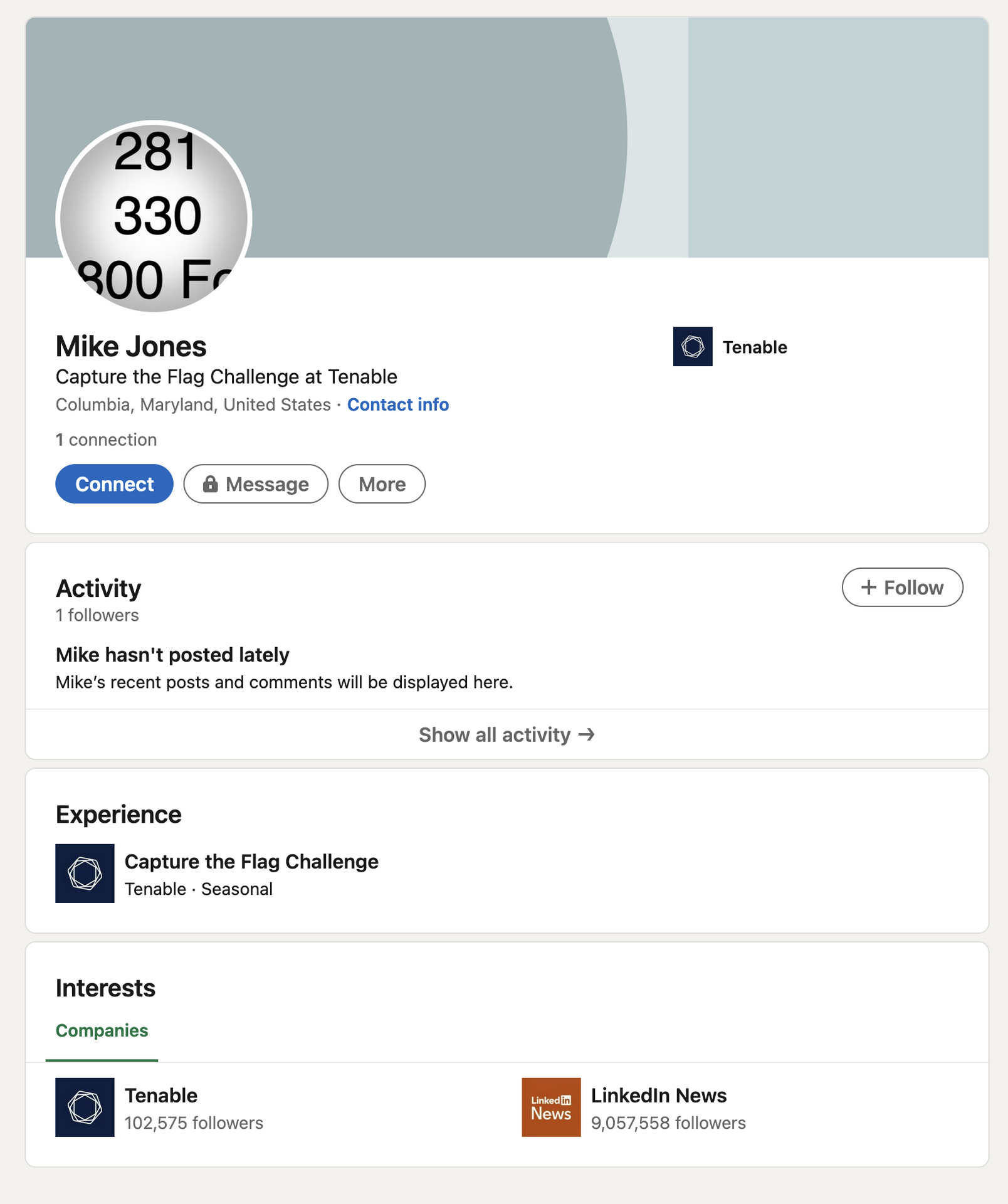
Then all people stuck as there is no much information we need, untill, very untill the Tenable updated the LinkedIn page and shows below:
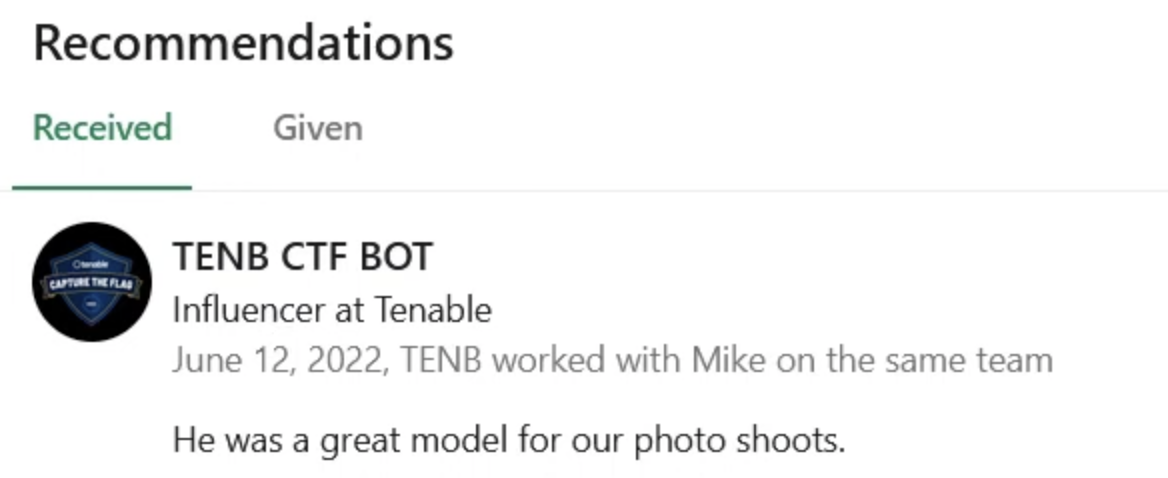
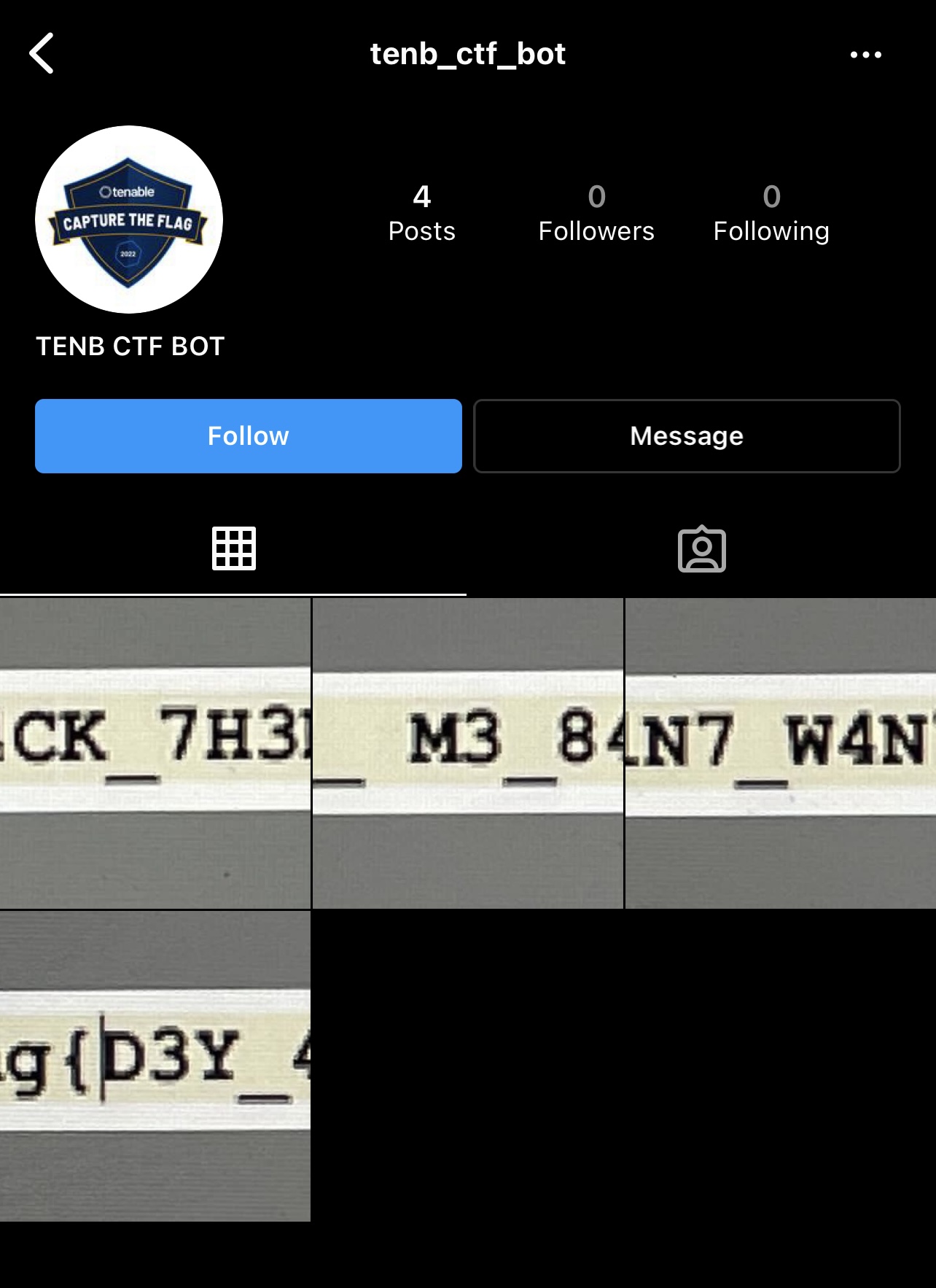
And related LinkedIn account TENB CTF BOT shows:
OK, now it’s simple to get the flag as we know MIKE JONES is reponsible for the phishing domain and his colleagues is TENB CTF BOT and he is an influencer and asked us to look at the photos.
Guess what’s that? It’s Instagram, of course.
Voilà.